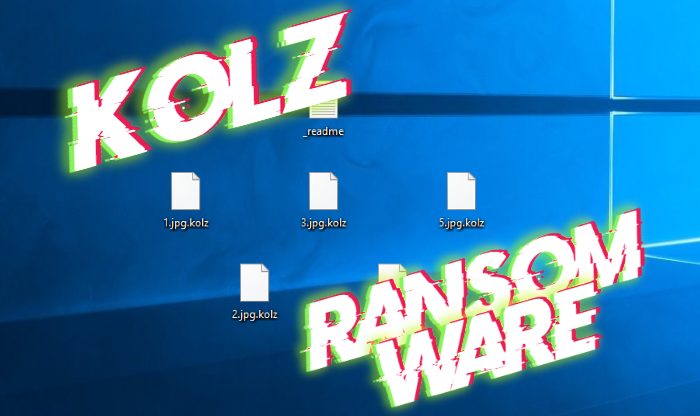
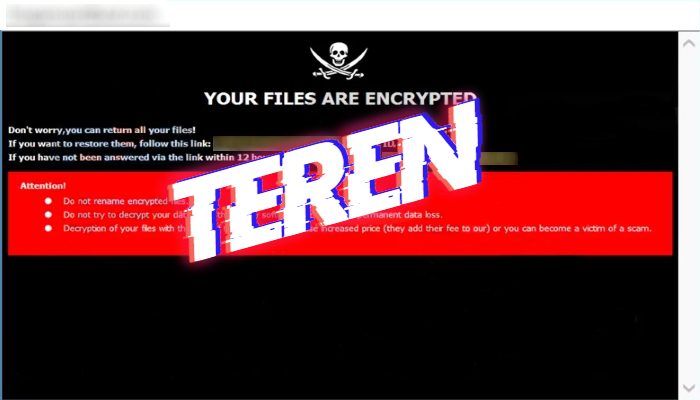
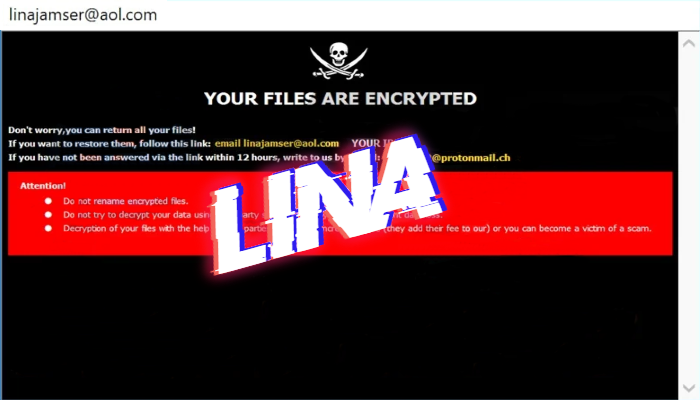
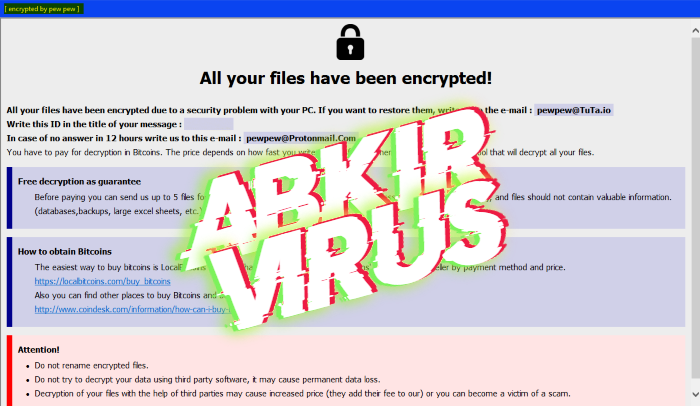
How to remove Kolz ransomware and decrypt “.kolz” files
What is “.kolz”? Computer viruses nowadays are very dangerous. There is a great amount of varieties which cause various damage. And the most dangerous type is ransomware viruses. And in this article we are going to tell you about the Kolz ransomware. This virus belongs to the STOP(DJVU) file-encryption ransomware and we can characterize this … Read more