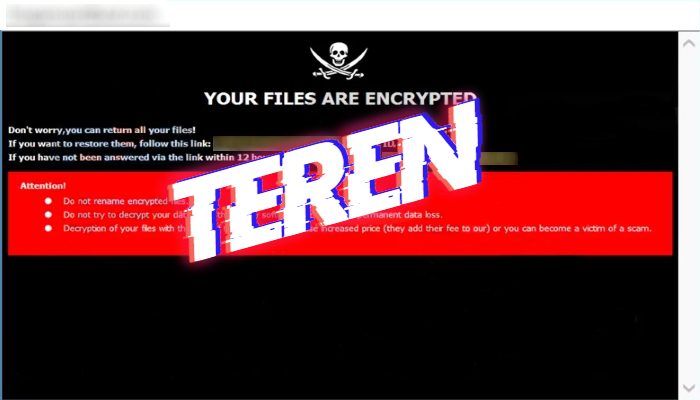
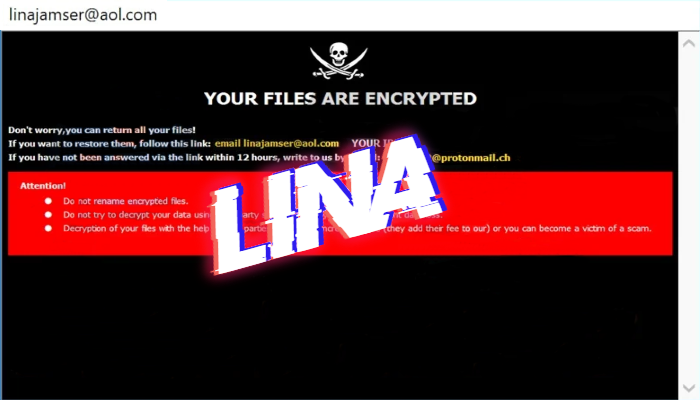
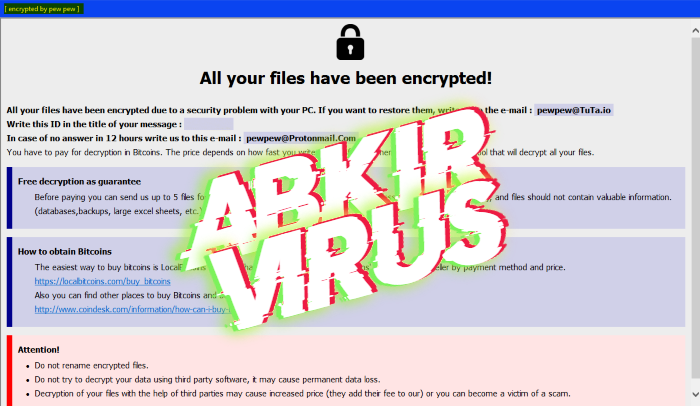
How to remove TEREN ransomware and decrypt “.TEREN” files
What does “.[Databack44@tuta.io].TEREN” extension mean? Nowadays, the internet is the one of the most important tools. However, it’s not safe at all, as every day hackers find new ways to get their profit. The one of the such threats is TEREN ransomware. This virus belongs to the Dharma file-encryption ransomware family. This family of viruses … Read more