Istatic.eshopcomp.com is a modern application for browser that can be installed without your participation. One day you just open your browser and realize that this browser add-on was downloaded. This situation will occur if you use some free programs from the web, as some browser add-ons can be installed with any other supplementary programs. At times these extra programs are viral or just undesirable. The browser add-on that can be added to your computer with this method is able to set the default settings of the browser, such as start page, search engine. If you are eager to remove Istatic.eshopcomp.com from the PC, in that case you are welcome to examine this article and perform the techniques.
Automatically Manually From browsers
Main features of SpyHunter:
- Deletes all elements created by Istatic.eshopcomp.com.
- Is able to solve browser problems and protect browser settings.
- Has System and Network Guards, so you can forget about malware.
What is Istatic.eshopcomp.com?
Istatic.eshopcomp.com is not harmful software as it cannot affect other computers, but it can be installed with different unknown programs. It makes a feeling that Istatic.eshopcomp.com is a PC infection.
But, in reality, it is just an nerve-racking add-on that tortures you with the help of advertising information in the form of popping-up windows. Almost every user has undesired browser add-ons like Istatic.eshopcomp.com and is eager to remove it.
1. Install Istatic.eshopcomp.com Removal Tool:

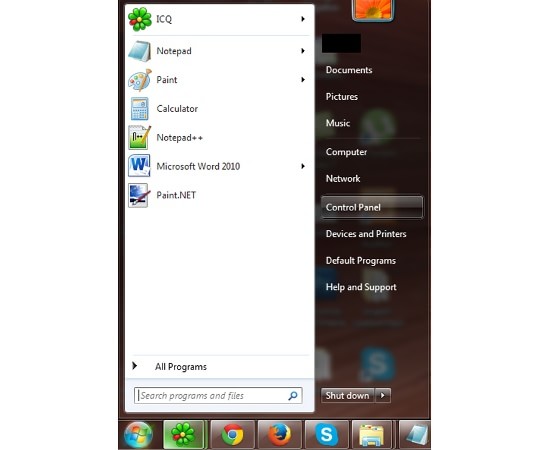
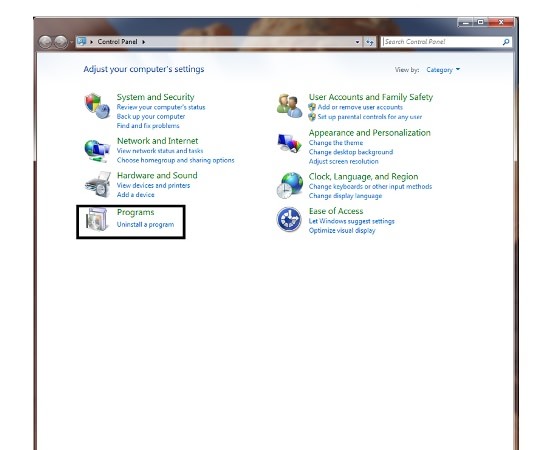
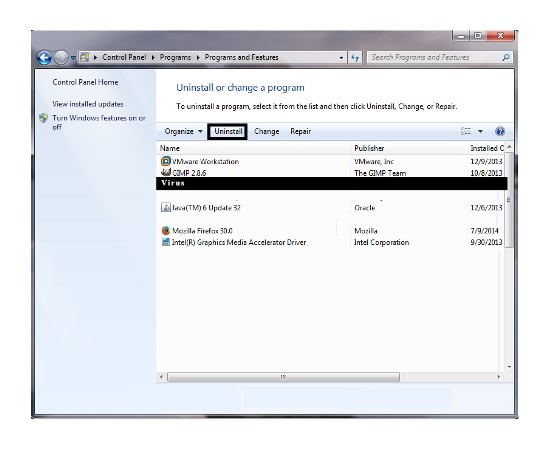
Step 1. Click Start button
Step 2. Click Control Panel
Step 3. Highlight the annoying software and select Uninstall
![]()
Files:
- No information
![]()
Folders:
- No information
![]()
Registry Entries:
- No information

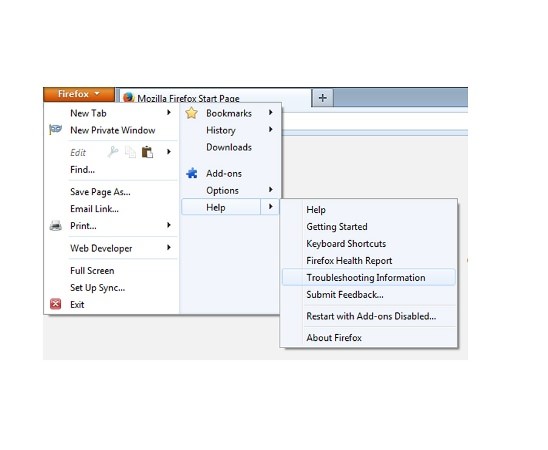
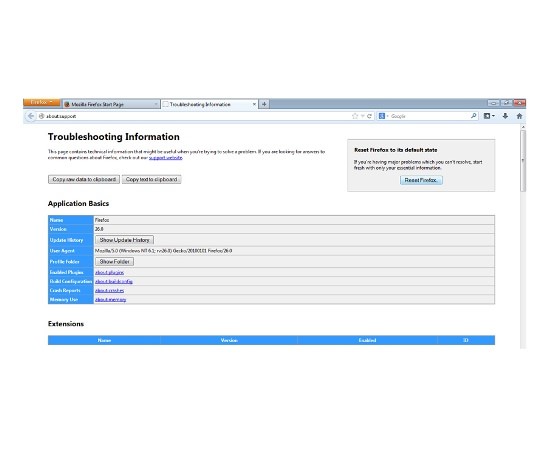
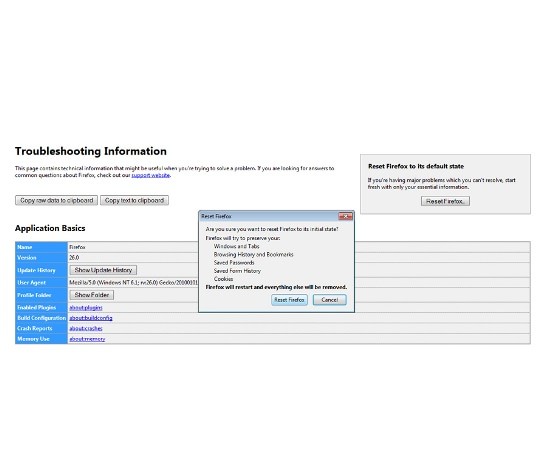
Uninstall Istatic.eshopcomp.com from Firefox:
- Help=>Troubleshooting Information
- Reset Firefox
- Finish

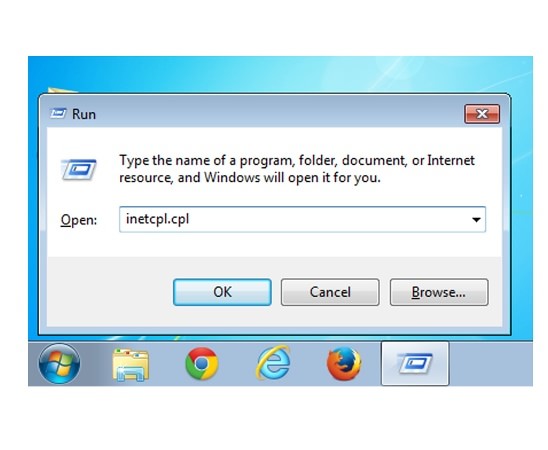
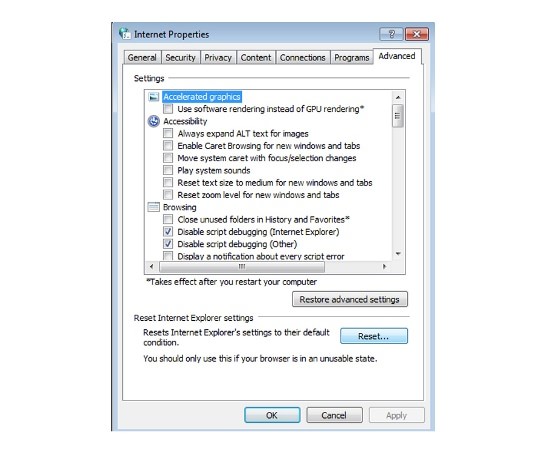
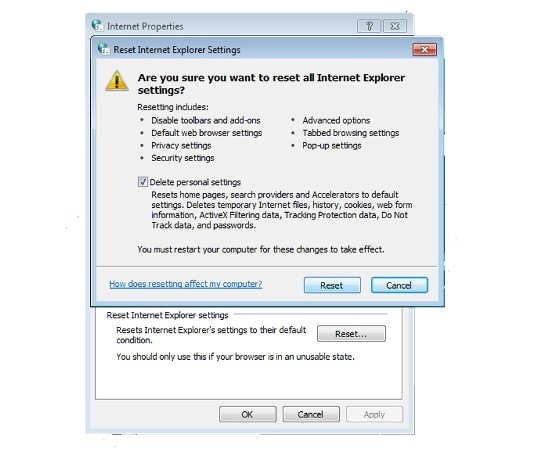
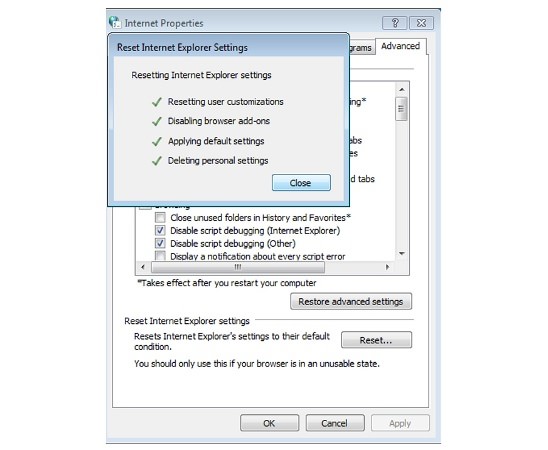
Delete Istatic.eshopcomp.com from IE:
- Run inetcpl.cpl
- Advanced=>Reset
- Delete Personal Settings=>Reset=>Close

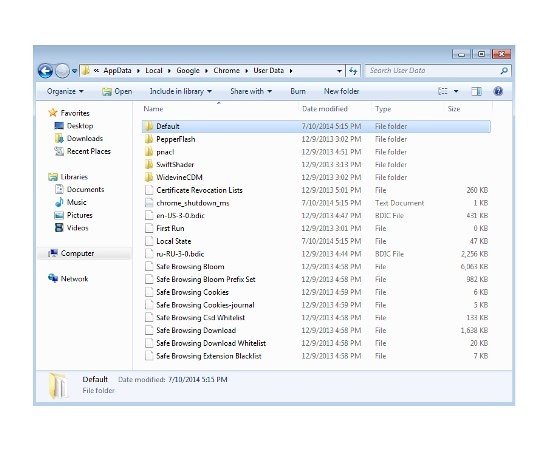
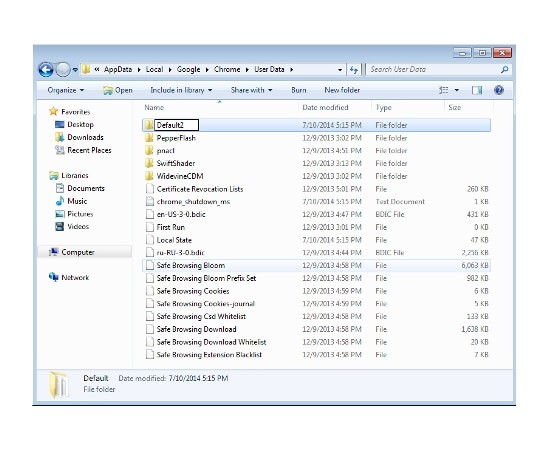
Remove Istatic.eshopcomp.com from Google Chrome:
- C:\Users\”your username”\AppData\Local\Google\Chrome\Application\User Data
- Rename Default folder to Default2
- Open Google Chrome
- Do not open Opera
- Remove Profile and Cache folders in:
- C:\Users\User_Name\AppData\Roaming\Opera Software\Opera Stable
- C:\Users\User_Name\AppData\Local\Opera Software\Opera Stable
- Open Opera
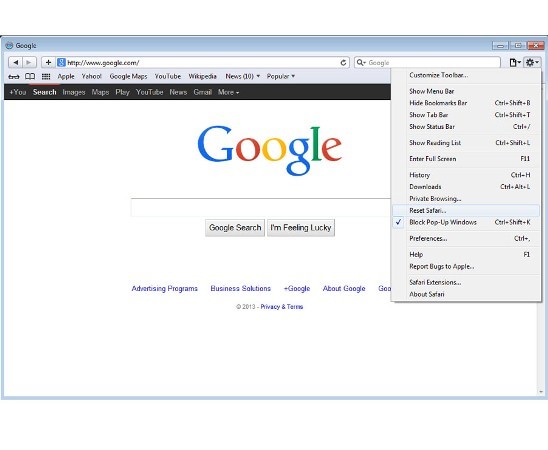
- Open your browser
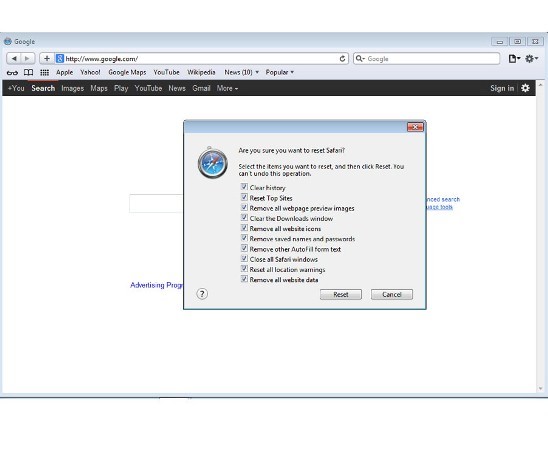
- Settings->Reset Safari
- Reset
It is all the same what add-on you want to install, it can be the vulnerability for your computer. Istatic.eshopcomp.com is not an exception. All browser vendors produce security patches and care about the safety of their users. But if you activate any extension, then vendors are not able to ensure that your system will not be infected. Online scammers can use the browser extension as it were a door to your PC. No doubt there is a sure effort to escape from this situation: download extensions from well-known and dependable vendors only. But is not an absolute defense from online delinquents and software infections. I advise not to have browser extensions at all.
You should be aware that any installed extension has already got the approval to use your sensitive data that you report when fill in some forms on-line. The reports, including your phone number, your name, your email, etc. Can be passed to some advertising companies. Be careful installing and using any browser add-ons and do not install them, if there is not a genuine want in it.
Istatic.eshopcomp.com, as a promotional extension, is more perilous, because there is no assurance that the promotional message is true and that the website that states in the ad is safe. If you want to make use of Istatic.eshopcomp.com or any other add-on that shows you special deals then you should be ready that it can cheat you.
| Damage Level |
Medium
(Potentially unwanted program) |
| Data Theft | 0,01% |
| System Failure | 0,2% |
| Manual Removal | 25 |
| Removal From Browsers | 38,3% |
| Removal with Free Antivirus | 43,2% |
| Removal with SpyHunter | 97,4% |
| Infected computers (USA) | 0,0004% |
| Infected computers (Europe) | 0,0003% |
| Browser Infection Probability | 54,3% |
Istatic.eshopcomp.com like all other adware programs has some main symptoms that will help you to define if your system is infected with it or not. Here is the list of them:
- Many block of ads shown by Istatic.eshopcomp.com
- Very sluggish computer
- Antimalware detects some dangers
- Some changes in the browser (toolbars, homepage, search engine)
- Search results are redirected
- Istatic.eshopcomp.com adds its files, folders and registry entries
Manual and Automatic Removal Methods?
You should know that manual ways of removal that uninstall Istatic.eshopcomp.com from browsers are absolutely secure and you can execute them not being afraid that you damage your computer. Also the instructions are productive, so you will reach the aim and the browser add-on will be removed together will all its manifestations. It is also an easy method; it yields merely to the automatic method of removal. But occasionally, using this method users are surprised that the PUP returns to the browser and they have to perform any other methods to delete it.
But manual technique that tells you to eliminate the files, folders and registry entries is the most risk one. If you risk to follow this way of removal, in this case you should remember only one simple: do not forget to create the backup of the registry. Also the technique should be performed just by the user that realizes what and why he should eliminate.In case you will delete several files or registry keys and values that do not belong to Istatic.eshopcomp.com, then your computer will not load next time. Experienced users will not be mistaken and can be delighted with the power of this manual way of removal.
Automatic technique is the method when a user installs any software to solve the problem. The way out is considered to be the most secure and powerful. It is also the easiest one. You should just find the antimalware scanner that has Istatic.eshopcomp.com in its signature base. This removal way is more helpful because you will install the antivirus program that will protect the computer from the future computer viruses.
Concerning the sums of money that users may pay for the removal of the virus I should say that some removal techniques are absolutely free, for example manual removal from browsers, manual professional removal (in the case if you will do it by yourselves), free antivirus software and the removal from Control Panel. But not all of them are effective. The information about the effectiveness of these methods I describe in the table that is called ‘Removal methods statistics’, you can see it below. Speaking about the paid ways of virus removal, I should enumerate the Computer Repair Shop Service and paid Antivirus software.
These methods are the most efficient. In spite of the great difference in the price (Repair Shop service depends on the complication of the problem and may cost up to $300, but paid antivirus costs up to $60) these removal techniques are almost equal in the effectiveness and in the results. I should also say that paid antiviruses always has support service (often free) that will remove the virus like in an expensive computer repair shop.
Removal methods statistics
| Removal method | Price | Effectiveness | Safety | Needed Time |
| Computer Repair Shop | $180-$240 | +++ | +++ | up to 4 days |
| Paid Antivirus | $35-70 | +++ | +++ | up to 1 hour |
| Free Antivirus |
$0 | +/- | +/- | up to 3 hours |
| From Control Panel | $0 | +/- | ++ | up to 1 hour |
| Manual Removal (Professional) | $0 | + | – | up to 4 Hours |
| Removal from browsers | $0 | +/- | +/- | up to 1 hour |
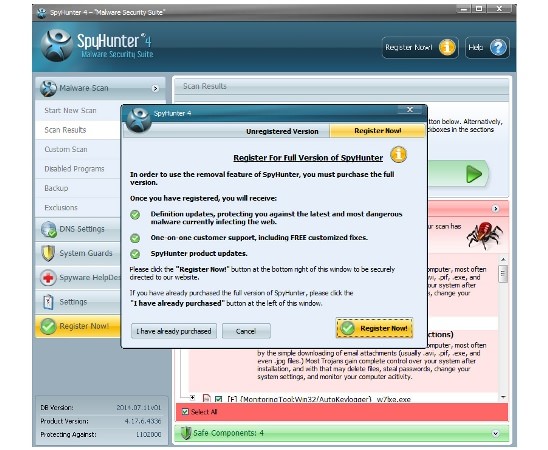
There are many useful tools and other antivirus software that can be downloaded to remove Istatic.eshopcomp.com and you can use any of them, but I recommend you SpyHunter. The program is the best Istatic.eshopcomp.com Removal Tool in my opinion. Removing the add-on you also will have a good chance to defend your PC.
Enigma Software created SpyHunter to be a efective antispyware and antimalware utility that can defend the system against all possible viruses, including rootkits and trojans. Owing to the regularly updated base of signatures SpyHunter uninstalls all the everyday viruses that are released by virus writers daily.
Then latest version of SpyHunter not only vary its interface to more handy and beautiful, but also the program does not conflict with other antispyware programs that you can download. Also the program works quicker and protects better.
SpyHunter gives real-time protection, has Integrated SpyHunter Compact OS that let to uninstall the most stubborn viruses and the dependable live technical support. SpyHunter is compatible with Windows 98/ME/NT/2000/XP/2003/Vista/Seven/8, it needs 256 MB of RAM, 75 MB of available hard disk space.
How to use SpyHunter
First of all you need to download SpyHunter on your PC. You can left-click the download link from this article. After that you should install SpyHunter like all possible antimalware utilities. I suppose that the antivirus tool can be installed easily and it is comprehensible for most foreign users due to the numerous languages that you can choose. This makes SpyHunter almost unquestioning leader among all other world antivirus utilities.
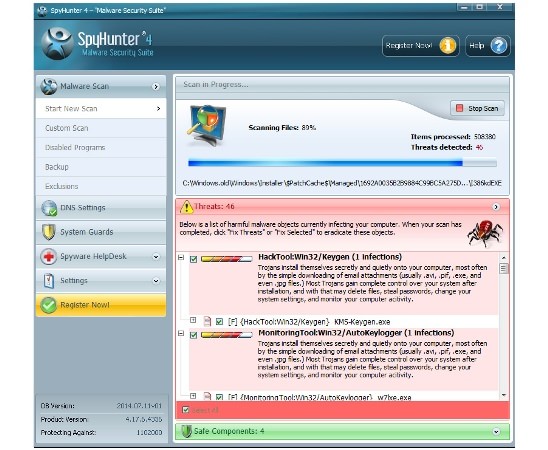
After installation, you should install its updates it, if the utility does not begin the update by itself when you load it for the first time. After the update it is time to begin the Scan process. In most common case it is enough to perform fast scan to define and uninstall all the computer threats and unwanted items in the system.
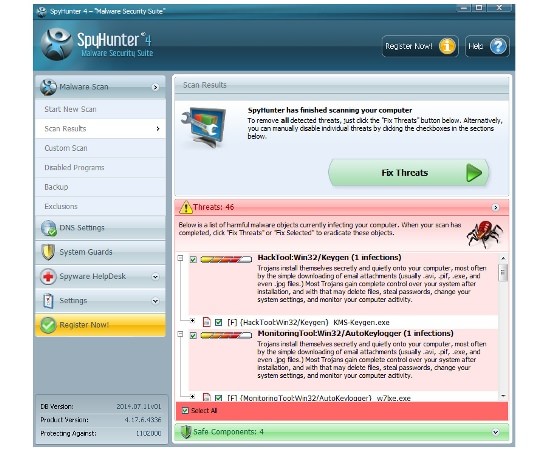
Examine the result when the scan will be ready. If there are some useful for you items in the list, so you can delete the tick near it, otherwise SpyHunter will delete the software. It deals with the uncommon and special software that users download for their work. But generally, there is no need to delete any ticks. Thereafter you should left-click Fix Threats button. If you have already purchased the license key, so the enumerated malware will be removed. In case you did not, then you will have the opportunity to pay for the license key.
I believe this guide was good for Istatic.eshopcomp.com Removal. But to protect your PC from next resembling programs for browsers and from all possible computer threats, so you are welcome to install any antivirus program. It is better to install an utility that has a large base of signatures, everyday update and real-time protection. Merely the software of this kind is able to keep the computer safe and sound. It is better to scan your system for computer threats at least once a week. Should have a extensive virus database and daily releases of updates. The most effective antivirus tools has real-time protection. It is the 100% guard that is able to reveal computer threats on the PC when it is just attempting to infect your PC.]
SpyHunter conforms to all the itemized demands. So, I believe it can protect the computer better than any other and also it can provide a real-time barrier to all the zero-day viruses. This program with comprehensible interface will scan your system. It will detect all the viruses and even all the possibly undesirable programs. If you installed any helpful utility for your work, but SpyHunter reveals it as the malicious program, but you are utterly certain that the utility cannot be malicious, so you can refer it to Exclusions and SpyHunter will not delete it and never will detect it as a malicious object any more. If you want to scan just separate file, so you are welcome to take advantage of Custom Scan option. You can also apply Process Guard or Registry Guard of the software for your accommodation.
I also want to advice you some helpful actions that will protect your system from Istatic.eshopcomp.com and other malicious objects in the future:
- Do not install any free of charge software from unknown vendors. If you do not like to pay for browser add-ons, then you should be very watchful during the installation of the software. You should not overlook the checkbox (usually small letters somewhere in the corner) that is responsible for the download of any other applications. You should uncheck this checkbox.
- Do not open any malicious websites (porn, for adults, websites of unknown free software), they usually contain some trojans or other types of computer threats.
- Do not use torrents or other sharing web services, because you can download malicious software instead of the wanted file.
- Do not double-click email attachment from unknown people. It can be a virus.
- Install any antivirus software and make a scan of your computer at least once a week.
About Author: Material provided by: Alesya Orlova

 Download SpyHunter right here
Download SpyHunter right here