What is PGPSnippet?
PGPSnippet is a dangerous virus that encodes users’ data. The main distribution of this virus is deceptive emails under the guise of invoices, tax bills, the social surveys, reward or other things that could be of interest to the user. Therefore, be very wary when receiving emails from unknown recipients. Do not open any attachments without checking it first with reliable antivirus. Compliance with this simple rule will help you avoid problems in the future. This ransomware is also distributed through fake software updates, torrent (P2P) networks, and trojans. After penetration, it immediately starts to encrypt sensitive files in the hidden mode so that the user can not notice anything suspicious. During encryption, each affected file gets .decodeme666@tutanota_com extension, for example, myfamily.jpg is changed to myfamily.jpg.decodeme666@tutanota_com. Upon completion of the process, it drops a ransom note (!!!README_DECRYPT!!!.txt), placing it on the desktop. In this article, you can learn how to remove PGPSnippet ransomware and decrypt .decodeme666@tutanota_com files.
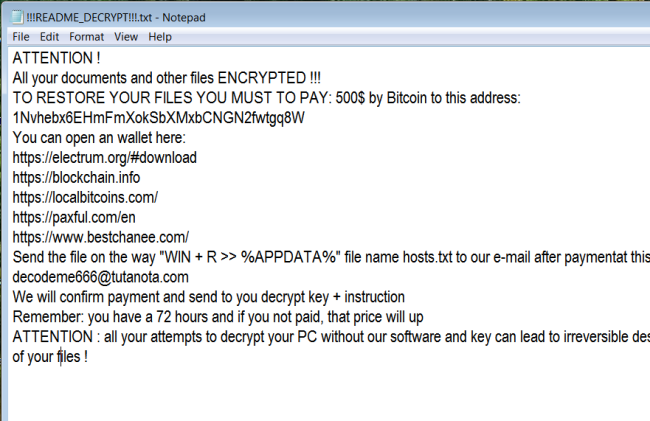
This is what PGPSnippet ransom note !!!README_DECRYPT!!!.txt contains:
ATTENTION !
All your documents and other files ENCRYPTED !!!
TO RESTORE YOUR FILES YOU MUST TO PAY: 500$ by Bitcoin to this address: 1Nvhebx6EHmFmXokSbXMxbCNGN2fwtgq8W
You can open an wallet here:
https://electrum.org/#download
https://blockchain.info
https://localbitcoins.com/
https://paxful.com/en
https://www.bestchanee.com/
Send the file on the way “WIN + R >> %APPDATA%” file name hosts.txt to our e-mail after paymentat this email address: decodeme666@tutanota.com
We will confirm payment and send to you decrypt key + instruction
Remember: you have a 72 hours and if you not paid, that price will up
ATTENTION : all your attempts to decrypt your PC without our software and key can lead to irreversible destruction
of your files !
Here is used a typical scheme of all ransomware-type viruses – to make victims pay them. The only differences between them are the ransom price (500$) and encryption method. Cybercriminals state that there are no ways to recover your files but to pay a ransom. Once payment is done, they are supposed to send you decryption key. But you should know that nobody can guarantee that they will fulfill their end of the bargain. The practice shows that cyber-criminals just ignore people who paid them. That’s why you should not be pushed about by them because you can remain without money and files. On the contrary, you only may encourage them to continue their dirty business. In any case, you will be simply scammed. That’s why there is no need to contact them, it wouldn’t help. Still, PGPSnippet ransomware does very complicated encryption, but it does not damage, move or delete your files, which means you have a chance to restore your personal data, but for now, you should focus on removing PGPSnippet ransomware.
How to remove PGPSnippet from your computer?
You may try to use anti-malware tool to remove PGPSnippet ransomware from your computer. Newly advanced ransomware detection technology is able to run an instant ransomware scan, which is perfect to protect your computer in case of a new ransomware attack.

How to decrypt files encrypted by PGPSnippet?
Decrypt .decodeme666@tutanota_com files manually
Once you’ve removed the virus, you are probably thinking of recovering files from encryption. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Restore data with automated decryption tools
Unfortunately, due to the novelty of PGPSnippet ransomware, there are no available automatic decryptors for this encryptor yet. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows saves copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.

