Nemty Ransomware encryption process
In this article we would like to tell you about Nemty ransomware. This type of malwares is called ransomwares, as these programs can change the structure of your files (encrypt) in order to make you pay for decryption. The infection process always proceeds unnoticed by the user, as hackers use some tricks: they put malwares into email attachments and usually directly attack your device by brute-forcing the definite ports. When the virus is successfully injected, it begins scanning process (it searches for your media files and documents) and then encrypts suitable files. After it, your files get another extension – .nemty. It means, that your files are unreadable now, as the structure of them cannot be read by your device. Don’t try to remove Nemty encryption by yourself, as it may lead to damaging of your data. As I have already mentioned, the purpose of these attacks is to make you pay the intruders for recovering your files. That’s why they also put a special ransom note, where you can find information about the virus and the contacts of the creators. If your device is infected with Nemty Ransomware, this file will be called NEMTY-DECRYPT.txt and it will contain the following message:
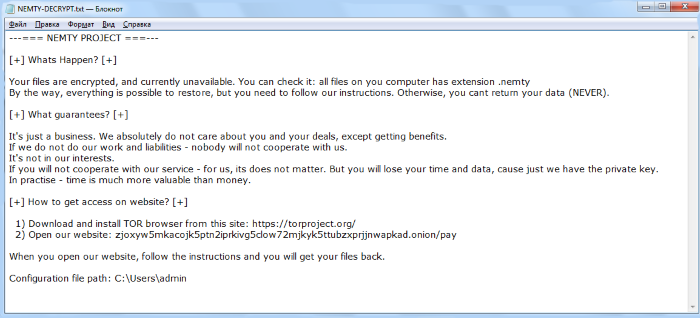
---=== NEMTY PROJECT ===---
[+] Whats Happen? [+]
Your files are encrypted, and currently unavailable. You can check it: all files on you computer has extension .nemty
By the way, everything is possible to restore, but you need to follow our instructions. Otherwise, you cant return your data (NEVER).
[+] What guarantees? [+]
It's just a business. We absolutely do not care about you and your deals, except getting benefits.
If we do not do our work and liabilities - nobody will not cooperate with us.
It's not in our interests.
If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key.
In practise - time is much more valuable than money.
[+] How to get access on website? [+]
1) Download and install TOR browser from this site: https://torproject.org/
2) Open our website: zjoxyw5mkacojk5ptn2iprkivg5clow72mjkyk5ttubzxprjjnwapkad.onion/pay
When you open our website, follow the instructions and you will get your files back.
Configuration file path: C:\Users\admin
As you can see, hackers directly say, that you don’t have any guarantee except of their words about cooperation. It’s easy for them to take your money and left you with your encrypted files alone. Moreover, the cost of their “services” is always too high, in any case don’t pay them a cent. Till the time there is a flow of money, hackers won’t stop to modify their old viruses and create new ones. If you wonder how to remove Nemty Ransomware and decrypt .nemty files, read our guide!
Article’s Guide
- How to remove Nemty Ransomware from your computer
- How to remove Nemty Ransomware encryption from your files
- Data Recovery
- Automated decryption tools
- Windows Previous Versions
How to remove Nemty Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove Nemty from your computer with all of its leftovers and register files.
Solution for Windows user: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like Nemty, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .Nemty files?
Once you’ve removed the virus, you are probably thinking how to decrypt .Nemty 1files. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Restore data with automated decryption tools
Unfortunately, due to the novelty of Nemty ransomware, there are no available automatic decryptors for this encryptor yet. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.


