Mockba ransomware encryption process
Mockba ransomware is the freshly made threat, that has been found recently. This ransomware belongs to the Estemani file-encryption ransomware family, that has a lot in common with STOP(DJVU) family: Nols, Werd, Ndarod, Leto, Bora; and Dhrama family: Money, Oo7 and CASH. This virus has been already very widespread, however the ways of its disseminating are not clear yet. That’s why we strongly recommend you to be more careful, when you are surfing the internet. The virus can be injected into a harmless file, that activates the malicious code once the file is opened. If you are already infected with it, you shall in no case try to remove Mockba encryption manually. Don’t modify the files without a detailed instruction, as it may damage your files and it’s like a gift from the heaven to restore even one of them.
The infection process may be described in this way: when the virus gets into the system, the two-step immediately occurs. It’s a background process, so it’s very difficult to understand in time, that your device is infected. The first step is the scanning process of all the folders on the hard drive and connected devices. Mockba ransomware looks for the documents and media files, as the virus aims at the preventing a user from the accessing to the valuable and sentimental files. When the files are found, Mockba encrypts them with a strong encryption algorithm. It also can be described as the modification of the structures, and the results of it are files, that are unreadable by the system. The sign of successful encryption is .mockba extension. Then the virus creates a ransom note called # HOW TO RECOVER YOUR DATA #.txt with the following information:
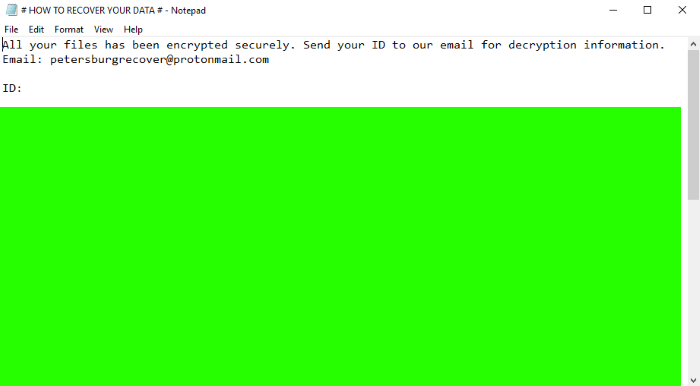
# HOW TO RECOVER YOUR DATA #.txt
All your files has been encrypted securely. Send your ID to our email for decryption information.
Email: petersburgrecover@protonmail.com
ID:
*ID*Avoid any contact with the ransoms! It’s a great risk to trust in them, as they are criminals. You can easily become twice a victim, as after the payment they can send you a malicious software instead of a decryption tool and corrupt your operating system! Moreover, it can be some kind of trojan, that will collect all information about you, steal your accounts and passwords, and then will attack your wallet. It’s obvious that your are to do something without their help. That’s why we’ve prepared the free guide on how to remove Mockba ransomware and decrypt .mockba files!
Article’s Guide
- How to remove Mockba Ransomware from your computer
- How to remove Mockba Ransomware encryption from your files
- Data Recovery
- Automated decryption tools
- Windows Previous Versions
How to remove Mockba Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove Mockba from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like Mockba, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .mockba files?
Once you’ve removed the virus, you are probably thinking how to decrypt .mockba files. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Restore data with automated decryption tools
Unfortunately, due to the novelty of Mockba ransomware, there are no available automatic decryptors for this encryptor yet. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Remove Mockba encryption with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.


