What does .mt88 stand for?
Every day users find new threats on the internet and one of them is MarkTrue88 ransomware. It belongs to the Matrix file-encryption ransomware family, the representatives of which such well known members as ABAT and DECP ransomwares. These viruses usually attack the devices being unnoticed by the users, as viruses of this family spread by the means of harmless files. Hackers inject the code of the viruses and this code executes once the user decides to open it. It’s possibly because of a number of backdoors in the operating system and software. These files can be easily found everywhere, as the more device hackers successfully infect, the better payment hackers can potentially get. Moreover, hackers can easily infect your device directly. They scan ports of the device and then brute force the password, with the help of which they have remote access to all functions and folders on your device. One more way of spreading of MarkTrue88 is email attachments. Hackers often write messages as if they are representatives of a well known company and attach to such letters questionable files. If your computer and server have been accidentally infected with MarkTrue88 ransomware, we should warn you not to try to decrypt .mt88 files or to remove MarkTrue88 ransomware manually, as it can potentially damage your system and data.
MarkTrue88 ransomware encryption process.
If MarkTrue88 ransomware successfully gets into the system, it will immediately begin the encryption process, that can be divided into two steps. At first the virus scans the system and all folders on the hard drive and server for the suitable for encryption files. These files are usually all formats of documents, media files and web files. However, it can possibly encrypt all files. When the files are found, MarkTrue88 begins to modify them and makes them unreadable. As the file structures have been modified the new extension .mt88 adds to them. Then the virus has to inform the user of the decryption services, the owners of which are the same persons. For this reason the virus creates ransom note, that is called !MT88_README!.rtf. Their words cannot be trusted. It’s not rare, when hackers get the payment and then stop all contacts with the victim or demand to pay them once again. Moreover, the situation can easily become much worse. Don’t waste your money and time! Follow our guide on how to remove MarkTrue88 ransomware and decrypt .mt88 files!
!MT88_README!.rtf
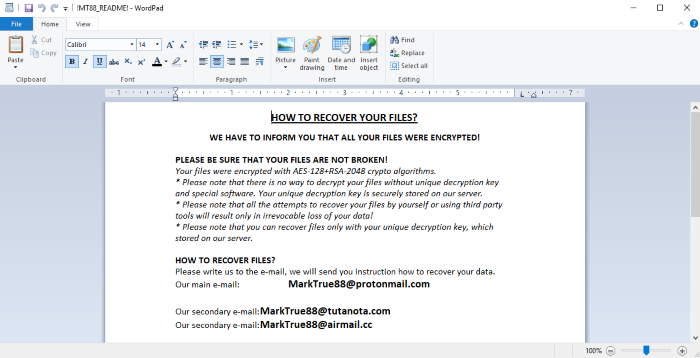
HOW TO RECOVER YOUR FILES?
WE HAVE TO INFORM YOU THAT ALL YOUR FILES WERE ENCRYPTED!
PLEASE BE SURE THAT YOUR FILES ARE NOT BROKEN!
Your files were encrypted with AES-128+RSA-2048 crypto algorithms.
* Please note that there is no way to decrypt your files without unique decryption key and special software. Your unique decryption key is securely stored on our server.
* Please note that all the attempts to recover your files by yourself or using third party tools will result only in irrevocable loss of your data!
* Please note that you can recover files only with your unique decryption key, which stored on our server.
HOW TO RECOVER FILES?
Please write us to the e-mail, we will send you instruction how to recover your data.
Our main e-mail: MarkTrue88@protonmail.com
Our secondary e-mail: MarkTrue88@tutanota.com
Our secondary e-mail: MarkTrue88@airmail.cc
Please write to our main e-mail. If you will not receive answer in 24 hours, please write to our secondary e-mails! Please always check SPAM folder!
* Write on English or use professional translator
In subject line write your personal ID: *ID*
For your assurance you can attach up to 3 small encrypted files to your message. We will decrypt and send you decrypted files for free.
* Please note that files must not contain any valuable information and their total size must be less than 5Mb.
Please don't worry, we can help you to RESTORE your server to original
state and decrypt all your files quickly and safely!
OUR HELP!
You have to pay for our help in Bitcoin Cryptocurrency.
Immidiately after payment we will send you (by e-mail) automatic decryption tool and your unique decryption key. You just have to start decryption tool on your server and all files will be automatically decrypted. All original file names will be restored too.
Article’s Guide
- How to remove MarkTrue88 Ransomware from your computer
- How to remove MarkTrue88 Ransomware encryption from your files
- Data Recovery
- Automated decryption tools
- Windows Previous Versions
How to remove MarkTrue88 Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove MarkTrue88 from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like MarkTrue88, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .mt88 files?
Once you’ve removed the virus, you are probably thinking how to decrypt .mt88 files. Let’s take a look at possible ways of decrypting your data.
Restore .mt88 files with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Decrypt .mt88 files with other software
Unfortunately, due to the novelty of MarkTrue88 ransomware, there are no decryptors that can surely decrypt encrypted files. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Decrypt .mt88 files with Emsisoft decryptor
This software includes information about more than 100 viruses of STOP(DJVU) family and other viruses. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.


