What is LeakThemAll Ransomware?
LeakThemAll ransomware is one of the delegates of numerous crypto viruses that have spread all over the world and are threatening ordinary users and large businesses and enterprises. This is an encryptor that encrypts files located on the user’s computer. As a rule, LeakThemAll ransomware touches exactly the class of files that is most significant for the user. For example, it encrypts photos, videos, audio, archives, and more. In addition, cryptovirus changes the extension of encrypted files to .crypt. So, for example, the examplefile.doc file becomes examplefile.doc.crypt, and so on. Consequently the pertinent question: how to remove LeakThemAll ransomware. Below we have indicated a text file READ_ME_NOW.htm that acts like a scam note:
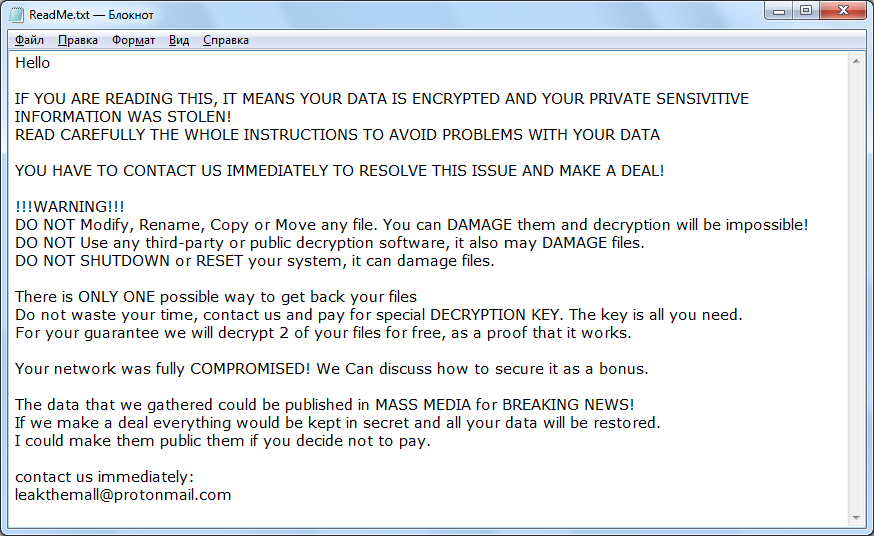
Hello
IF YOU ARE READING THIS, IT MEANS YOUR DATA IS ENCRYPTED AND YOUR PRIVATE SENSIVITIVE INFORMATION WAS STOLEN!
READ CAREFULLY THE WHOLE INSTRUCTIONS TO AVOID PROBLEMS WITH YOUR DATA
YOU HAVE TO CONTACT US IMMEDIATELY TO RESOLVE THIS ISSUE AND MAKE A DEAL!
!!!WARNING!!!
DO NOT Modify, Rename, Copy or Move any file. You can DAMAGE them and decryption will be impossible!
DO NOT Use any third-party or public decryption software, it also may DAMAGE files.
DO NOT SHUTDOWN or RESET your system, it can damage files.
There is ONLY ONE possible way to get back your files
Do not waste your time, contact us and pay for special DECRYPTION KEY. The key is all you need.
For your guarantee we will decrypt 2 of your files for free, as a proof that it works.
Your network was fully COMPROMISED! We Can discuss how to secure it as a bonus.
The data that we gathered could be published in MASS MEDIA for BREAKING NEWS!
If we make a deal everything would be kept in secret and all your data will be restored.
I could make them public them if you decide not to pay.
contact us immediately:
leakthemall@protonmail.com
According to the contents of this note, the user needs to perform several operations through the Tor browser, and then pay 500-1500 US dollars for decrypting the data. Of course, if you take into account all the many such crypto viruses, $ 500-1500 is not very much for someone, however, you do not need to pay. The explanation is simple – there is no guarantee that you will take your files in their initial condition. Do not take chances. Use our suggestions and instructions to remove LeakThemAll ransomware and decrypt .crypt files.
Article’s Guide
- How to remove LeakThemAll ransomware from your computer
- Automatically remove LeakThemAll ransomware
- Manually remove LeakThemAll ransomware
- How to decrypt .LeakThemAll files
- Automatically decrypt .LeakThemAll files
- Manually decrypt .LeakThemAll files
- How to prevent ransomware attacks
- Remove LeakThemAll ransomware and decrypt .LeakThemAll files with our help
How to remove LeakThemAll ransomware from your computer?
Every day ransomware viruses change as well as their folders, executable files and the processes, which they use. For this reason it’s difficult to detect the virus yourself. That’s why we’ve prepared the detailed guide for you on how to remove LeakThemAll ransomware from your computer!
Automatically remove LeakThemAll ransomware
We strongly recommend you to use automated solution, as it can scan all the hard drive, ongoing processes and registry keys. It will mitigate the risks of the wrong installation and will definitely remove LeakThemAll ransomware from your computer with all of its leftovers and register files. Moreover, it will protect your computer from future attacks.
Our choice is Norton 360 . Norton 360 scans your computer and detects various threats like LeakThemAll virus, then removes it with all of the related malicious files, folders and malicious registry keys. Moreover, it has a great variety of other features, like protection from specific ransomware attacks, safe box for your passwords and many other things!

Manually remove LeakThemAll ransomware
This way is not recommended, as it requires strong skills. We don’t bear any responsibility for your actions. We also warn you that you can damage your operating system or data. However, it can be a suitable solution for you.
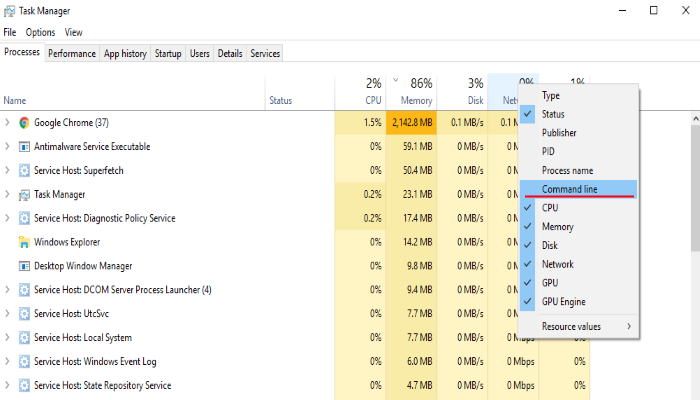
- Open the “Task Manager”
- Right click on the “Name” column, add the “Command line”
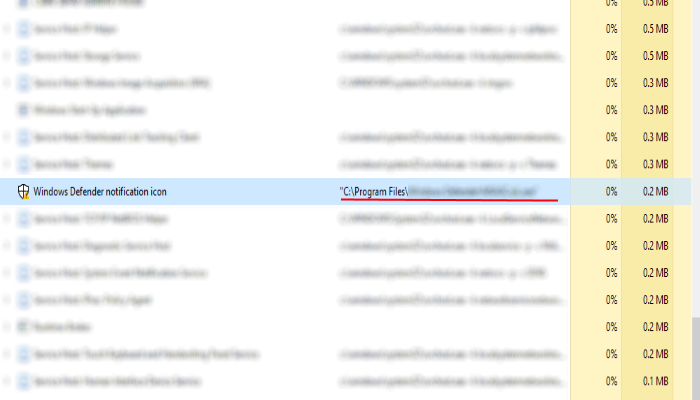
- Find a strange process, the folder of which probably is not suitable for it
- Go To the process folder and remove all files
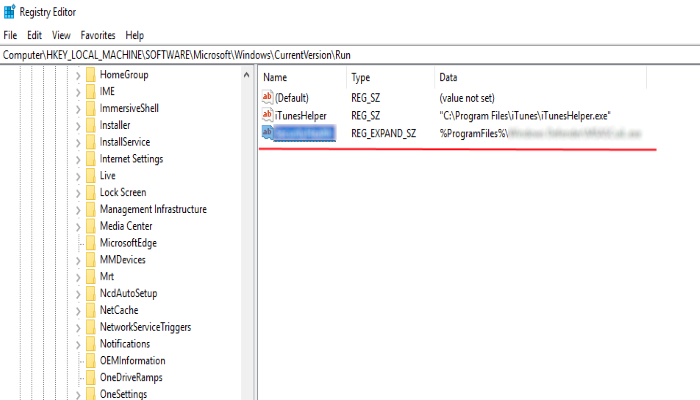
- Go to the Registry and remove all keys related to the process
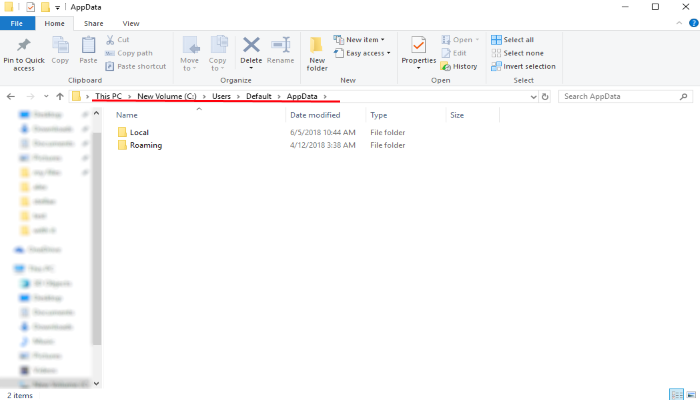
- Go to the AppData folder and remove all strange folders, that you can find
How to decrypt .LeakThemAll files?
Restore .LeakThemAll files with Stellar Data Recovery

- Download and install Stellar Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Other solutions
The services we’ve mentioned in this part also guarantee users, that the encrypted data is unlikely to become damaged. But you should understand, that there is still a risk to corrupt your files.
Decrypt .LeakThemAll files with Emsisoft decryptor
Decrypt .LeakThemAll files with Kaspersky decryptors
Decrypt .LeakThemAll files with Dr. Web decryptors
Decrypt .LeakThemAll files manually
If above mentioned solutions didn’t help to decrypt .LeakThemAll files, still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Restore .LeakThemAll files with Windows Previous Versions
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore .LeakThemAll files with System Restore
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
How to prevent ransomware attacks?
If you have successfully removed LeakThemAll ransomware, you know probably think about the ways how to protect your data from future attacks. The best way is to create backups of your data. We recommend you to use only high-quality products. Our choice here is Stellar Data Recovery. This soft can easily create highly-qualified backups, has a user-friendly interface and moreover, it can help you to restore your files! Then you should take strict control of all your internet connections. Some of the ransomware viruses connect to various internet services and can even infect computers that are connected to the same local network.
CONCLUSION: nowadays, these solutions are all possible ways to remove LeakThemAll ransomware and decrypt “.LeakThemAll” files. Nowadays the best way to remove it is the Norton 360 . Their specialists improve the scanning system and update the databases every day. It helps not only to remove existing problems but also protects computers from future attacks. If there is a new way to decrypt your files, we will update the article, so stay tuned.