Article’s Guide
- What does .Horriblemorning stand for?
- Horriblemorning ransomware encryption process.
- How to remove Horriblemorning Ransomware from your computer
- How to decrypt .Horriblemorning files
- Data Recovery
- Automated decryption tools
- Other software
What does .horriblemorning stand for?
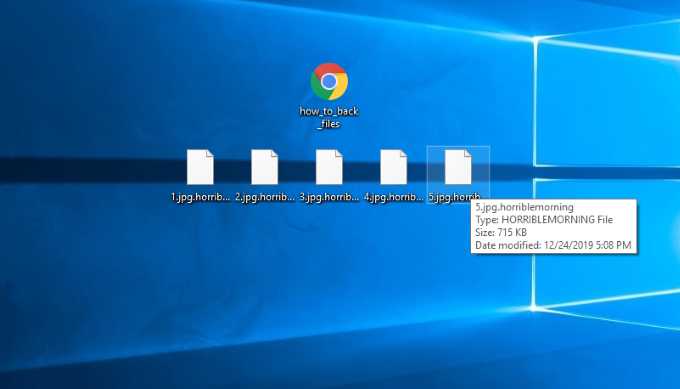
Horriblemorning is one of the newest threats, that internet surfers face. This virus is a part of GlobeImposter file-encryption ransomware family. This family includes such viruses as CILLA, StuardRitchi, Sill@tuta.io and AD ransomwares. The developers of this virus, as we guess, are “Corporate Tears” team. As a rule Horriblemorning ransomware spreads by the means of “coffman.exe” file and attacks corporate networks. In order to execute it, nowadays hackers widely use ScreenConnect service, that gives them almost full control over computers. However, there are other ways of spreading this virus, such as fake emails and fake installators. By the meaning of falsifying they try to make victims feel comfortable to open such files. That’s why it’s very difficult to recognize a potential attack of Horriblemorning ransomware. If you are unlucky and your network is infected with this virus, don’t try to remove Horriblemorning and decrypt .horriblemorning files manually! Every changing of an encrypted file may lead to unrestorable damage of this file!
Horriblemorning encryption process.
The encryption process, that Horriblemorning ransomware executes, makes several steps. At first the virus adds some registry keys and tries to make the system think, that it’s a legitimate process. Then the virus hides itself in order to avoid noticing by antivirus protection. When it’s done, Horriblemorning begins to search for suitable files to encrypt. These files are usually all formats of media files, documents, databases and archives. As the final step it modifies the file structures and makes the files unreadable. As the result the files get new extension – .horriblemorning. In order to force the victims to pay for the decryption, the criminals left ransom note, that is called – how_to_back_files.html. The only one method to surely decrypt these files is to get the decryption key from the criminals. However, we strongly recommend you to avoid any contact with them, as there is no any firm guarantee, that they will really help you. The hackers can easily stop any contact with you, once they’ve been paid or even to damage your system. That’s why we’ve made the detailed guide on how to remove Horriblemorning and decrypt .horriblemorning files!
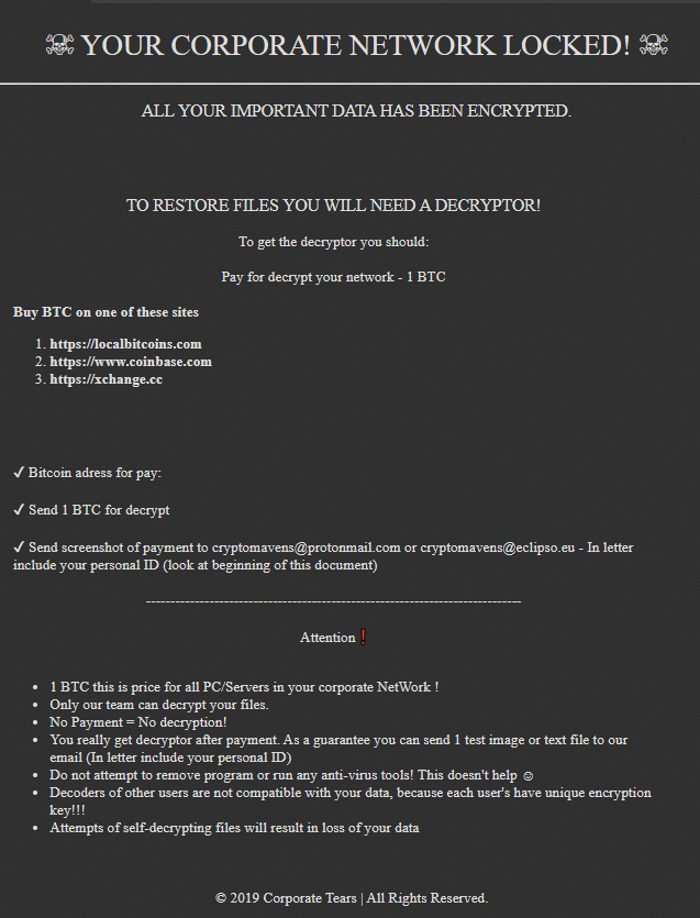
how_to_back_files.html
YOUR PERSONAL ID
*ID*
ENGLISH
? YOUR CORPORATE NETWORK LOCKED! ?
ALL YOUR IMPORTANT DATA HAS BEEN ENCRYPTED.
TO RESTORE FILES YOU WILL NEED A DECRYPTOR!
To get the decryptor you should:
Pay for decrypt your network - 1 BTC
Buy BTC on one of these sites
hxxps://localbitcoins.com
hxxps://www.coinbase.com
hxxps://xchange.cc
Bitcoin adress for pay: *address*
Send 1 BTC for decrypt
Send screenshot of payment to cryptomavens@protonmail.com or cryptomavens@eclipso.eu - In letter include your personal ID (look at beginning of this document)
-----------------------------------------------------------------------------
Attention
1 BTC this is price for all PC/Servers in your corporate NetWork !
Only our team can decrypt your files.
No Payment = No decryption!
You really get decryptor after payment. As a guarantee you can send 1 test image or text file to our email (In letter include your personal ID)
Do not attempt to remove program or run any anti-virus tools! This doesn't help ?
Decoders of other users are not compatible with your data, because each user's have unique encryption key!!!
Attempts of self-decrypting files will result in loss of your data
© 2019 Corporate Tears | All Rights Reserved.
How to remove Horriblemorning Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove Horriblemorning from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like Horriblemorning, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .Horriblemorning files?
Once you’ve removed the virus, you are probably thinking how to decrypt .Horriblemorning files or at least restore them. Let’s take a look at possible ways of decrypting your data.
Restore .Horriblemorning files with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Decrypt .Horriblemorning files with other software
Unfortunately, due to the novelty of Horriblemorning ransomware, there are no decryptors that can surely decrypt encrypted files. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Decrypt .Horriblemorning files with Emsisoft decryptor
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.