Article’s Guide
- What does .Deniz_Kizi stand for?
- Deniz_Kizi ransomware encryption process.
- How to remove Deniz_Kizi Ransomware from your computer
- How to decrypt .Deniz_Kizi files
- Data Recovery
- Automated decryption tools
- Other software
What does .Deniz_Kizi stand for?
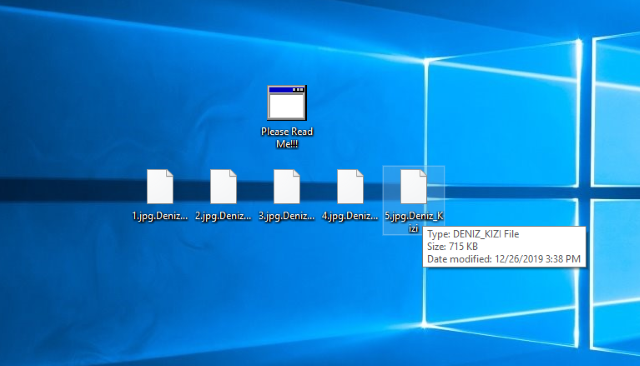
Recently, Deniz_Kizi ransomware has been modified. This virus is a file-encryption ransomware, the function of which, as it can be understood, is to prevent a victim from the accessing to definite file formats by the means of file encryption. At the present moment this virus spreads by the means of “No1.exe” file, that can potentially be found everywhere on the internet. Hackers can easily spread it by the means of file sharing services and torrent trackers. However, nowadays ScreenConnect service becomes more and more popular among hackers. By the means of this soft hackers can easily make necessary changes in an operating system and to install Deniz_Kizi virus remotely and unnoticed. However, they still use such popular methods as fake emails and installators. These methods aim at tricking potential victims into infection computers by the means of opening such files. That’s why it’s strongly advised to have a strong antivirus protection. If your computer is already infected, we are to warn you: don’t try to remove Deniz_Kizi ransomware and decrypt .Deniz_Kizi files without any special tool! Every change made by users themselves can potentially damage files.
Deniz_Kızı ransomware encryption process.
When Deniz_Kızı achieves an operating system, it immediately begins to make changes in the operating system and memory. Then it starts the root process and tries to identify a virtual machine and creates a number of various files. Then it searches for files to encrypt and modifies them. As the rule the suitable files are all formats of media files, documents, databases and archives. As the result the files get new extension – .Deniz_Kizi. The last step that it makes is a disabling of the Task Manager. During the encryption process Deniz_Kizi is also creating ransom note called – Please Read Me!!!.hta. By the means of this note hackers try to assure victims, that everything can be easily restored with one payment. Unfortunately, due to the novelty of this virus, there is no a decryptor, that can decrypt all your files surely. The easiest way is to get a decryptor from the criminals. However, it’s a usual thing for them to stop all contacts with the victims after the payment. Moreover, they can easily send to a victim other virus instead of the decryption tool. We advise you not to try to contact with them! Still, there is a hope to restore your files. That’s why we’ve prepared the guide on how to remove Deniz_Kizi ransomware and decrypt .Deniz_Kizi files!
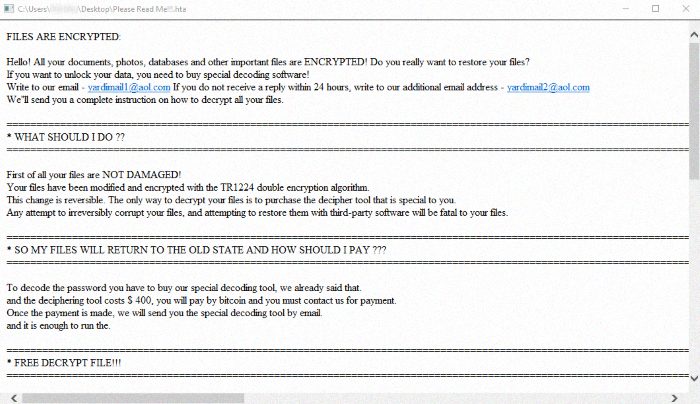
Please Read Me!!!.hta
FILES ARE ENCRYPTED:
Hello! All your documents, photos, databases and other important files are ENCRYPTED! Do you really want to restore your files?
If you want to unlock your data, you need to buy special decoding software!
Write to our email - yardimail1@aol.com If you do not receive a reply within 24 hours, write to our additional email address - yardimail2@aol.com
We"ll send you a complete instruction on how to decrypt all your files.
=========================================================
* WHAT SHOULD I DO ??
=========================================================
First of all your files are NOT DAMAGED!
Your files have been modified and encrypted with the TR1224 double encryption algorithm.
This change is reversible. The only way to decrypt your files is to purchase the decipher tool that is special to you.
Any attempt to irreversibly corrupt your files, and attempting to restore them with third-party software will be fatal to your files.
=========================================================
* SO MY FILES WILL RETURN TO THE OLD STATE AND HOW SHOULD I PAY ???
=========================================================
To decode the password you have to buy our special decoding tool, we already said that.
and the deciphering tool costs $ 400, you will pay by bitcoin and you must contact us for payment.
Once the payment is made, we will send you the special decoding tool by email.
and it is enough to run the.
=========================================================
* FREE DECRYPT FILE!!!
=========================================================
Free decryption as warranty!
If you don"t believe in our service and want to see proof, you can ask us about the test for decryption.
You send us up to 2 encrypted files.
Use the file sharing service and Win-Rar to send files for testing. Files must be smaller than 1 MB (unarchived) and Files should not matter! Do not send us databases, backups or large excells. Files etc. We will decrypt and send back your decrypted files as proof!
=========================================================
* HOW TO BUY BITCOINS ???
=========================================================
Bitcoins have two simple ways:
Link1: hxxps://exmo.me/en/support#/1_3
Link2: hxxps://localbitcoins.net/guides/how-to-buy-bitcoins
Read the information in these links carefully, because you may need to buy even large quantities.
Note: Use translation for Turkish source.
=========================================================
!!! ATTENTION !!!
!!! If you do not pay within 2 days, you will not be able to recover your files forever.
!!! Do not rename encrypted files.
!!! Do not attempt to decrypt your data using third-party software, as this may cause permanent data loss.
!!! Unraveling your files with the help of third parties can lead to increased prices and don"t trust anyone even your dog.
=========================================================
* THE KEY REQUIRED FOR THE DECRYPT TOOL
Don"t change these 2 key decryption tool for this 2 key required !!!
and please note that these 2 keys are encrypted with the AES-256 encryption system.
*Keys*
How to remove Deniz_Kizi Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove Deniz_Kizi from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like Deniz_Kizi, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .Deniz_Kizi files?
Once you’ve removed the virus, you are probably thinking how to decrypt .Deniz_Kizi files or at least restore them. Let’s take a look at possible ways of decrypting your data.
Restore .Deniz_Kizi files with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Decrypt .Deniz_Kizi files with other software
Unfortunately, due to the novelty of Deniz_Kizi ransomware, there are no decryptors that can surely decrypt encrypted files. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Decrypt .Deniz_Kizi files with Emsisoft decryptor
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.