What is ALKA?
The one of the newest internet threats everyone can possibly face is ALKA ransomsomware. This virus belongs to the STOP(DJVU) file-encryption ransomware family, the members of which are such viruses as BBOO, REPP, NPSG, BTOS, TOPI, REHA, NOSU, PORET and KODC ransomwares. This family is one of the most widespread ones, due to the ways the viruses spread. In case of ALKA ransomware, the most widely used one is various executable files, which are shared through free file sharing services and torrent trackers. However, hackers can easily make fake websites, that looks like the original ones and by the means of various notifications they try to lure potential victims into downloading of such files. However, hackers also often attack the Remote Access Ports and inject ALKA ransomware manually. That’s why it’s necessary to have a strong antivirus protection nowadays, that is able to prevent such attacks and remove ALKA ransomware before it’s been executed.
When the ALKA is in the system, it changes some keys in the Registry and tries to inject itself into regular system processes. This step is required as the virus tries to stay unnoticed by the built-in system protection. Then the virus scans the hard drive and looks for the suitable for encryption files. Nowadays ALKA attacks only media files and documents, however, it can be updated and get the ability to attack other file formats. When the files are found, ALKA begins to modify file structures and makes the files unreadable. The clearest sign of the infection with this virus is “.alka” extension, which is added to names of files. Then the virus drops the ransom note, called “_readme.txt”. By the means of this note hackers promote their decryption services and unfortunately, it’s the surest way nowadays to decrypt your files. However, often criminals don’t respond to the messages after being paid. Moreover, they often send malware and viruses instead of the decryptor. That’s why we strongly recommend you to avoid any contact with them and prepared the guide on how to remove ALKA ransomware and decrypt .alka files.
_readme.txt
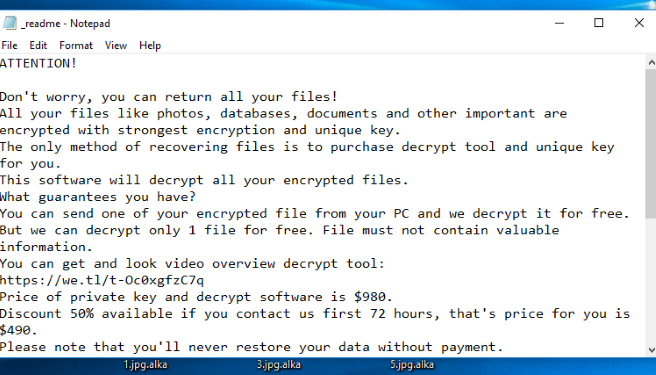
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-Oc0xgfzC7q
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@firemail.cc
Reserve e-mail address to contact us:
helpmanager@iran.ir
Your personal ID:
*ID*
Article’s Guide
- How to remove ALKA Ransomware from your computer
- How to decrypt .alka files
- Data Recovery
- Automated decryption tools
- Other software
How to remove ALKA Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove ALKA ransomware from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like ALKA, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .alka files?
Once you’ve removed the virus, you are probably thinking how to decrypt .alka files or at least restore them. Let’s take a look at possible ways of decrypting your data.
Restore .alka files with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Decrypt .alka files with other software
Unfortunately, due to the novelty of ALKA ransomware, there are no decryptors that can surely decrypt encrypted files. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Decrypt .alka files with Emsisoft decryptor
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.



ESTOU COM ESTE PROBLEMA DO ALKA MAS NA INFORMATICA DIZEM QUE É IMPOSSIVEL RESTAURAR.
COMO FAÇO PARA OBTER SEUS SERVIÇOS
Hello! We’ve written, that the SUREST way to decrypt data is to get the hackers’ decryptor, however, there are still other solutions, that can help you. There are no undecryptable files.
Unfortunately, nowadays we don’t provide any services, besides those that have been already mentioned in the article :(. But in the near future – will do.